A digital certificate (also known as public key certificate) is an electronic document used to prove the ownership of a public key.
Within it, contains a number of data items, including:
- The sender’s public key
- Date of creation and expiry
- (Certificate) serial number
- Certificate Authority (that issued the certificate)
- Subject name (name of user/owner, computer, network device)
- Hashing algorithm (data or signature) e.g. SHA2
PKI (Public Key Infrastructure)
- PKI is a set of software and hardware infrastructures to ensure the authenticity of users, companies and data
- PKI involves trusted third parties (on both sides) who can verify the integrity and ownership (authenticity) of a public key.
- This is called a certification authority (CA)
Obtaining / Using a Digital Certificate
- The digital cert is used to authenticate the receiver is who they are saying they are
- Most of the time people refer to ‘Bob and Alice’ or ‘Person A/B’ but also ‘Company’
- Person A (the receiver) who wants to receive secure messages, generates a Private Key pair and contacts a certificate authority (CA)
- The CA confirms the identity of Person A
- Person A then sends their public key to the CA
- The CA creates a public key certificate (digital certificate), and writes Person A’s public key into the certificate (item of data)
- The CA then uses its own private key to create a digital signature to the document
- The digital certificate is given to Person A
- Person A posts the digital certificate on a website
- A person wishing to use Person A’s public key will download the digital cert and use the CA’s public key to extract Person A’s public key
Digital Signature
-
A digital signature is a mathematical scheme for demonstrating the authenticity of digital messages or documents. A document’s unique fingerprint
-
A valid digital signature gives a recipient reason to believe that the:
- message was created by a known sender (authentication)
- sender cannot deny having sent the message (non-repudiation)
- the message was not altered in transit (integrity)
-
They are commonly used for:
- Software transmission
- Financial transactions
- Other applications where detection of forgery or tampering is important
-
A digital signature is used to verify a message / transaction
-
The recipient can check if the message was tampered with by hashing the received message and comparing this value with the decrypted signature
- The hash is a digest. A digest is not an encrypted version of the plain text, but a numerical summary of its contents, unique to the document
-
To decrypt the signature, the corresponding public key is required
-
Digital signatures can be sent with encrypted or plain text documents / messages
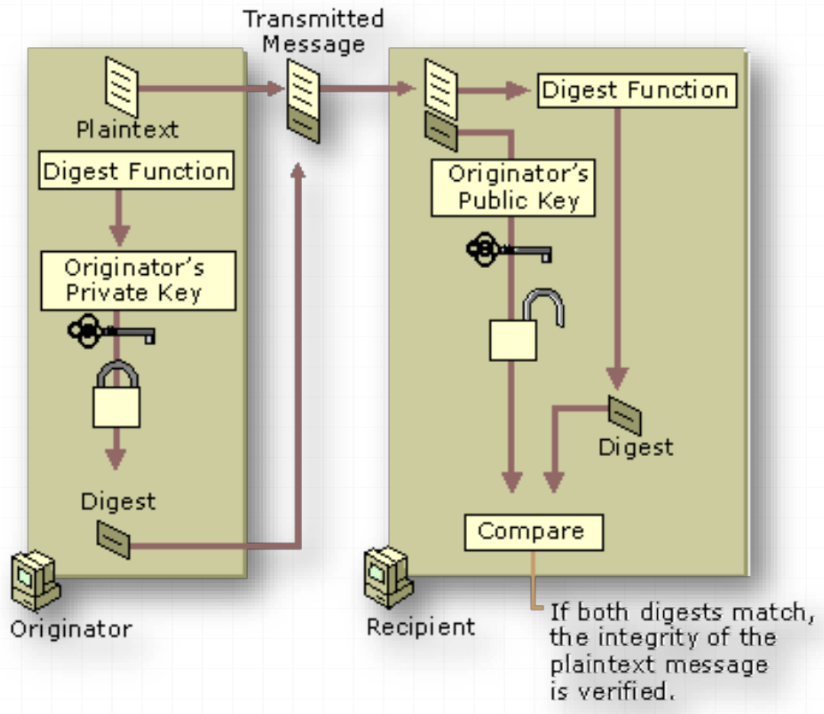
-
Digest of plaintext message created by sender
-
Digital signature created by encrypting digest with sender’s private key
-
Receiving user compares received digest with a digest created based on the received document
-
If both are the same, the message is:
- Unaltered in transmission
- Originating from the sender (as only they have their private key)
-
Message Digest
- A message digest is a fixed size, numerical version of the contents of a message.
- A message digest is created by a hash function.
- The digest is sent along with the message itself.